Recently I was working on a fresh install of Pritunl’s VPN server on a VM. Pritunl’s software is free for simple configurations and is a really easy way to setup a VPN server in a few minutes – it’s also compliant with OpenVPN standards so you can use either the ubiquitous OpenVPN client or Pritunl’s own branded client. The Pritunl client has some advantages like easy one-step configuration with a similarly configured Pritunl server (vs importing a settings files) but otherwise they are largely functionally the same.
One of the new features that was recently (within the last year?) added to Pritunl was the ability to use Let’s Encrypt certificates in the server. Previously, you had to either get a third-party plugin or run Pritunl behind a reverse proxy to get Let’s Encrypt or any other certificate working (without upgrading to a more expensive paid license).
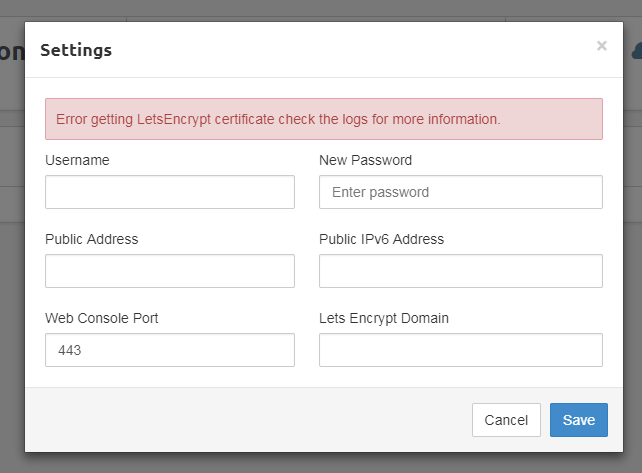
However, the Let’s Encrypt function wasn’t working. Normally, you would set the domain name for the certificate in the settings dialog box, then hit “Save” and the backend would run and verify the domain, fetch the certificate, and apply it all automatically.
Now, I’m just getting “Error getting LetsEncrypt certificate check the logs for more information.”
Okay, lets take a look at the logs:
[patient-plateau-8521][2017-11-16 16:08:58,851][INFO] Parsing acme account key...
[patient-plateau-8521][2017-11-16 16:08:58,981][INFO] Parsing acme CSR...
[patient-plateau-8521][2017-11-16 16:08:59,075][INFO] Registering acme account...
[patient-plateau-8521][2017-11-16 16:08:59,850][ERROR] Failed to get LetsEncrypt cert
Traceback (most recent call last):
File "/usr/lib/pritunl/local/lib/python2.7/site-packages/pritunl/handlers/settings.py", line 711, in settings_put
acme.update_acme_cert()
File "/usr/lib/pritunl/local/lib/python2.7/site-packages/pritunl/acme.py", line 49, in update_acme_cert
cert = get_acme_cert(settings.app.acme_key, csr)
File "/usr/lib/pritunl/local/lib/python2.7/site-packages/pritunl/acme.py", line 24, in get_acme_cert
app.set_acme,
File "/usr/lib/pritunl/local/lib/python2.7/site-packages/pritunl/acme_tiny.py", line 111, in get_crt
raise ValueError("Error registering: {0} {1}".format(code, result))
ValueError: Error registering: 400 {
"type": "urn:acme:error:malformed",
"detail": "Provided agreement URL [https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf] does not match current agreement URL [https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf]",
"status": 400
}
acme_domain = u'this.is.my.domain'
Oh…great. Um, it looks like there’s a problem with the agreement URL which are basically the Terms of Service for using Let’s Encrypt. The solution was actually very easy.
SSH into the sever and edit the main configuration file:
/usr/lib/pritunl/local/lib/python2.7/site-packages/pritunl/settings/app.py
In my config, it was on line 124. Edit the line to the newest agreement and save and close.
'acme_agreement_url': 'https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf',
Re-compile the Python binary and restart the Pritunl server, then try setting your domain name again.
sudo python -m compileall . sudo service pritunl restart
This time it worked like a charm for me. Done!